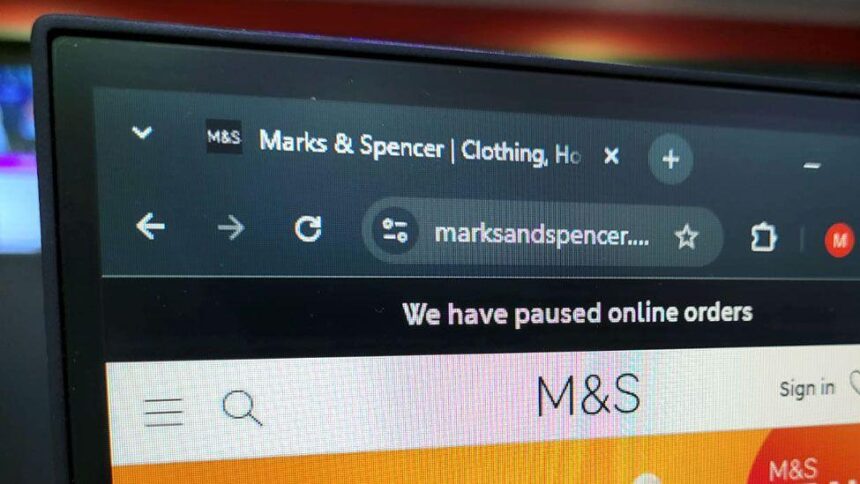
As of May 1, M&S remains in recovery mode. While physical stores are still open, the company’s digital services have yet to be restored.
Online orders through the M&S website and app remain paused. Click & Collect, gift cards, and Sparks loyalty points are either unavailable or unreliable.
Many customers are still being refunded for failed orders placed before the system went down. Some in-store and contactless payment systems are partially working again, but results vary widely by location.
The company has yet to release any formal statement—no press update, no CEO address, and no timeline for full restoration.
One thing we do know is that M&S has already removed all job listings from its careers site. Just a week ago, there were more than 200 active vacancies. Now, there are none.
Inside the company, the move is being treated as a practical step—M&S is focusing all its energy on fixing its digital systems, steadying day-to-day operations, and finding out exactly what went wrong. Recruitment can wait, said one insider. “Right now, it’s about containment and control.”
M&S’s market value has already dropped by more than £650 million, driven by a sustained fall in its share price. Lost online revenue may exceed £30 million, and operational costs continue to rise by the day.
The cost of recovery is expected to run into the tens of millions, covering everything from cybersecurity experts and forensic investigations to legal advice and rebuilding IT systems. And that’s before any potential fines—if customer data was compromised, the Information Commissioner’s Office (ICO) could step in with serious penalties.
Who Was Behind the Attack?
Marks & Spencer has not officially named the culprits, but cybersecurity experts increasingly point to Scattered Spider, also known as Octo Tempest.
This group, known for targeting major corporations, uses a combination of social engineering and technical sophistication to gain access to internal systems.
They typically impersonate employees to breach help desks, bypass multi-factor authentication through manipulation, and deploy ransomware to lock down systems while extracting sensitive data.
With a track record that includes high-profile attacks on MGM Resorts and Caesars Entertainment, M&S would represent their most prominent UK retail victim to date—if attribution is confirmed.
In the coming days, M&S is expected to begin a phased recovery. The company will likely reactivate online food and fashion orders first, followed by systems for processing returns and refunds.
Loyalty programs like Sparks may take longer to bring back online, given their integration with account data and purchase history.
A public post-incident report or official statement is expected soon, especially if regulators push for transparency. Customers affected by disruptions to gift cards or Click & Collect services may also receive compensation, though nothing has been announced yet.
M&S is also expected to ramp up its cybersecurity investment. Analysts believe this breach will prompt other UK retailers to do the same.
With the May 21 earnings report approaching fast, investors are watching closely for hard numbers and a clear recovery roadmap.